About Osueta?
Osueta it's a simple Python 2 script to exploit the OpenSSH User Enumeration Timing Attack, present in OpenSSH versions <= 7.2 and >= 5.*. The script has the ability to make variations of the username employed in the bruteforce attack, and the possibility to establish a DoS condition in the OpenSSH server.
Read more: OpenSSH User Enumeration Time-Based Attack
The bug was corrected in OpenSSH version 7.3.
Authors of Osueta:
- c0r3dump3d: coredump@autistici.org
- rofen: rofen@gmx.de
Osueta's Installation
For Linux users, open your Terminal and enter these commands:
If you're Windows users, follow these steps:
- Install Python 2.7.x from Python.org first. On Install Python 2.7.x Setup, choose Add python.exe to Path.
- Download Osueta-master zip file.
- Then unzip it.
- Open CMD or PowerShell window at the Osueta folder you have just unzipped and enter these commands:
pip install python-nmap paramiko IPypython osueta.py -h
Advice: Like others offensive tools, the authors disclaims all responsibility in the use of this script.
Osueta help menu:
Osueta's examples:
A single user enumeration attempt with username variations:
python2 osueta.py -H 192.168.1.6 -p 22 -U root -d 30 -v yesA single user enumeration attempt with no user variations a DoS attack:
python2 osueta.py -H 192.168.1.6 -p 22 -U root -d 30 -v no --dos yesScanning a C class network with only one user:
python2 osueta.py -H 192.168.1.0/24 -p 22 -U root -v no Scanning a C class network with usernames from a file, delay time 15 seconds and a password of 50000 characters:
python2 osueta.py -H 192.168.1.0/24 -p 22 -L usernames.txt -v yes -d 15 -l 50Read more
FACEBOOK Messenger has become an exceptionally popular app across the globe in general. This handy app comes with very interactive and user-friendly features to impress users of all ages.
With that being said, there are a lot of people who are interested in knowing how to hack Facebook Messenger in Singapore, Hong Kong and other places. The requirement to hack Facebook Messenger arises due to various reasons. In this article, we are going to explain how to hack Facebook Messenger with ease.
As you may know, Facebook Messenger offers a large range of features. Compared to the initial release of this app, the latest version shows remarkable improvement. Now, it has a large range of features including group chats, video calls, GIFs, etc. A lot of corporate organizations use Facebook messenger as a mode of communication for their marketing purposes. Now, this messenger app is compatible with chatbots that can handle inquiries.
Why Hack Facebook Messenger in Singapore?
You may be interested in hacking Facebook Messenger in Singapore (or anywhere else) for various reasons. If you suspect that your partner is having an affair, you may want to hack Facebook Messenger. Or, if you need to know what your kids are doing with the messenger, you will need to hack it to have real time access.
You know that both of these situations are pretty justifiable and you intend no unethical act. You shouldn't hack Facebook Messenger of someone doesn't relate to you by any means, such a practice can violate their privacy. Having that in mind, you can read the rest of this article and learn how to hack Facebook Messenger.
How to Hack Someone's Facebook Messenger in Singapore
IncFidelibus is a monitoring application developed by a team of dedicated and experienced professionals. It is a market leader and has a customer base in over 191+ countries. It is very easy to install the app, and it provides monitoring and hacking of Facebook for both iOS and Android mobile devices. You can easily hack into someone's Facebook messenger and read all of their chats and conversations.
Not just reading the chats, you can also see the photo profile of the person they are chatting to, their chat history, their archived conversations, the media shared between them and much more. The best part is that you can do this remotely, without your target having even a hint of it. Can it get any easier than this?

No Rooting or Jailbreaking Required
IncFidelibus allows hacking your target's phone without rooting or jailbreaking it. It ensures the safety of their phone remains intact. You don't need to install any unique rooting tool or attach any rooting device.
Total Web-Based Monitoring
You don't need to use any unique gadget or app to track activity with IncFidelibus. It allows total web-based monitoring. All that you need is a web browser to view the target device's data and online activities.
Spying With IncFidelibus in Singapore
Over ten years of security expertise, with over 570,000 users in about 155+ countries, customer support that can be reached through their website, and 96% customer satisfaction. Need more reasons to trust IncFidelibus?
Stealth Mode
IncFidelibus runs in pure Stealth mode. You can hack and monitor your target's device remotely and without them knowing about it. IncFidelibus runs in the background of your target's device. It uses very less battery power and doesn't slow down your phone.
Hacking Facebook Messenger in Singapore using IncFidelibus
Hacking Facebook Messenger has never been this easy. IncFidelibus is equipped with a lot of advance technology for hacking and monitoring Facebook. Hacking someone's Facebook Messenger is just a few clicks away!
Track FB Messages in Singapore
With IncFidelibus, you can view your target's private Facebook messages and group chats within a click. This feature also allows you to access the Facebook profile of the people your target has been interacting with. You can also get the media files shared between the two.
Android Keylogger
IncFidelibus is equipped with a powerful keylogger. Using this feature, you can record and then read every key pressed by your target on their device.
This feature can help get the login credentials of your target. You can easily log into someone's Facebook and have access to their Facebook account in a jiffy.

What Else Can IncFidelibus Do For You?
IncFidelibus control panel is equipped with a lot of other monitoring and hacking tools and services, including;
Other Social Media Hacking
Not just FB messenger, but you can also hack someone's Instagram, Viber, Snapchat, WhatsApp hack, SMS conversations, call logs, Web search history, etc.
SIM card tracking
You can also track someone SIM card if someone has lost their device, changed their SIM card. You can get the details of the new number also.
Easy Spying Possible with IncFidelibus
Monitoring someone's phone is not an easy task. IncFidelibus has spent thousands of hours, had sleepless nights, did tons of research, and have given a lot of time and dedication to make it possible.
@HACKER NT
Related news
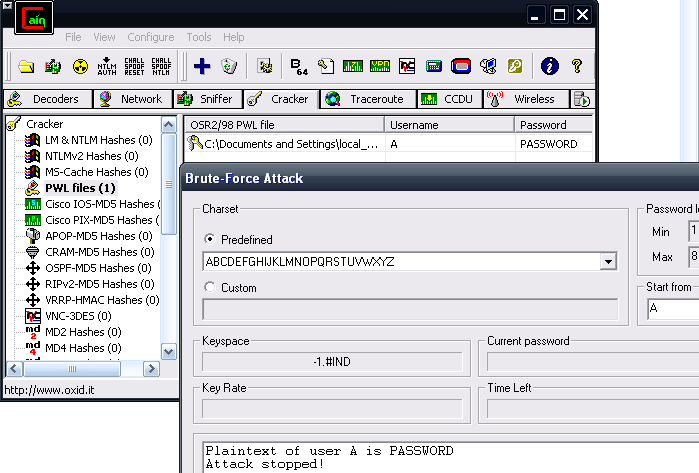
The first thing we can do when we have read access to the Windows directory through the share, is to locate all the *.pwl files on the c:\windows directory, copy them to your machine where Cain is installed, switch to Cracker tab, pwl files, load the pwl file, add username based on the filename, and try to crack it. If you can't crack it you might still try to add a .pwl file where you already know the password in the remote windows directory. Although this is a fun post-exploitation task, but still, no remote code execution. These passwords are useless without physical access.
- there is no "at" command (available since Windows 95 plus!)
- there is no admin share
- there is no RPC
- there is no named pipes
- there is no remote registry
- there is no remote service management
During my quest for a tool to hack Windows 95, I came across some pretty cool stuff:
But the best of the best is Fluxay, which has been written by chinese hackers. It is the metasploit from the year 2000. A screenshot is worth more than a 1000 words. 4 screenshot > 4 thousand words :)
But at the end, no remote code execution for me.
Don't try to download the Winsocks 2 patch from the official MS site, it is not there anymore, but you can download it from other sites.
After staring it for minutes, turned out it is constant, no new processes appeared.
Looking at the next screenshot, one can notice this OS was not running a lot of background processes ...
- You are lucky and not the plain Windows 95 is installed, but Windows 95 Plus! The main difference here is that Windows 95 Plus! has built-in scheduler, especially the "at" command. Just overwrite a file which is scheduled to execution, and wait. Mission accomplished!
- Ping of death - you can crash the machine (no BSOD, just crash) with long (over 65535 bytes) ICMP ping commands, and wait for someone to reboot it. Just don't forget to put your backdoor on the share and add it to autoexec.bat before crashing it.
- If your target is a plain Windows 95, I believe you are out of luck. No at command, no named pipes, no admin share, nothing. Meybe you can try to fuzz port 137 138 139, and write an exploit for those. Might be even Ping of Death is exploitable?
Now we can replace diskalm.exe with our backdoor executable, and wait maximum one hour to be scheduled.
Instead of a boring text based tutorial, I created a YouTube video for you. Based on the feedbacks on my previous tutorialz, it turned out I'm way too old, and can't do interesting tutorials. That's why I analyzed the cool skiddie videoz, and found that I have to do the followings so my vidz won't suck anymore:
- use cool black windows theme
- put meaningless performance monitor gadgets on the sidebar
- use a cool background, something related with hacking and skullz
- do as many opsec fails as possible
- instead of captions, use notepad with spelling errorz
- there is only one rule of metal: Play it fuckin' loud!!!!
Read more
About OWASP-ZSC
OWASP ZSC is open source software written in python which lets you generate customized shellcodes and convert scripts to an obfuscated script. This software can be run on Windows/Linux/OSX with Python 2 or 3.
What is shellcode?: Shellcode is a small codes in Assembly language which could be used as the payload in software exploitation. Other usages are in malwares, bypassing antiviruses, obfuscated codes...
You can read more about OWASP-ZSC in these link:
- OWASP ZSC Tool Project - OWASP
- Document: OWASP ZSC · GitBook (Legacy)
- Home page: OWASP ZSC | OWASP ZCR Shellcoder
- Features: OWASP ZSC | OWASP ZCR Shellocder Available Features
- Archive: ZCR-Shellcoder-Archive
- Mailing List: Google Groups
- API: api.z3r0d4y.com
Another good reason for obfuscating files or generating shellcode with OWASP-ZSC is that it can be used during your pen-testing. Malicious hackers use these techniques to bypass anti-virus and load malicious files in systems they have hacked using customized shellcode generators. Anti-virus work with signatures in order to identify harmful files. When using very well known encoders such as
msfvenom, files generated by this program might be already flagged by Anti-virus programs.Our purpose is not to provide a way to bypass anti-virus with malicious intentions, instead, we want to provide pen-testers a way to challenge the security provided by Anti-virus programs and Intrusion Detection systems during a pen test.In this way, they can verify the security just as a black-hat will do.
According to other shellcode generators same as Metasploit tools and etc, OWASP-ZSC using new encodes and methods which antiviruses won't detect. OWASP-ZSC encoders are able to generate shell codes with random encodes and that allows you to generate thousands of new dynamic shellcodes with the same job in just a second, that means, you will not get the same code if you use random encodes with same commands, And that make OWASP-ZSC one of the best! During the Google Summer of Code we are working on to generate Windows Shellcode and new obfuscation methods. We are working on the next version that will allow you to generate OSX.
OWASP-ZSC Installation:
You must install Metasploit and Python 2 or 3 first:
- For Debian-based distro users:
sudo apt install python2 python3 metasploit-framework - For Arch Linux based distro users:
sudo pacman -S python2 python3 metasploit - For Windows users: Download Python and Metasploit here.
sudo):DISCLAIMER: THIS SOFTWARE WAS CREATED TO CHALLENGE ANTIVIRUS TECHNOLOGY, RESEARCH NEW ENCRYPTION METHODS, AND PROTECT SENSITIVE OPEN SOURCE FILES WHICH INCLUDE IMPORTANT DATA. CONTRIBUTORS AND OWASP FOUNDATION WILL NOT BE RESPONSIBLE FOR ANY ILLEGAL USAGE.
An example of OWASP-ZSC
More info
About Medusa
Medusa is a speedy, parallel, and modular, login brute-forcer. The goal is to support as many services which allow remote authentication as possible. The author considers following items as some of the key features of this application:
Thread-based parallel testing. Brute-force testing can be performed against multiple hosts, users or passwords concurrently.
Flexible user input. Target information (host/user/password) can be specified in a variety of ways. For example, each item can be either a single entry or a file containing multiple entries. Additionally, a combination file format allows the user to refine their target listing.
Modular design. Each service module exists as an independent
.mod file. This means that no modifications are necessary to the core application in order to extend the supported list of services for brute-forcing.Multiple protocols supported. Many services are currently supported (e.g. SMB, HTTP, MS-SQL, POP3, RDP, SSHv2, among others).
See doc/medusa.html for Medusa documentation. For additional information:
Building on macOS
#getting the source
git clone https://github.com/jmk-foofus/medusa
cd medusa
#macOS dependencies
brew install freerdp
$ export FREERDP2_CFLAGS='-I/usr/local/include'
$ export FREERDP2_LIBS='-I/usr/local/lib/freerdp'
#building
./configure
make
#executing
./src/medusa
Medusa's InstallationMedusa is already installed on Kali Linux, Parrot Security OS, BlackArch and any other Linux distros based for security pentesting purposes.
For Debian-based distro users, open your Terminal and enter this command:
sudo apt install medusaFor Arch Linux-based distro users, enter this command:
sudo pacman -S medusaAbout the author:
- Email: jmk@foofus.net
- Github: jmk-foofus
- Website: Foofus.net
- BruteDum: Brute Force attacks SSH, FTP, Telnet, PostgreSQL, RDP, VNC with Hydra, Medusa and Ncrack
- FTPBruter: A FTP Server Brute forcing tool written in Python 3
- Blazy - Crack Website Logins in seconds with Bruteforce attacks
- SocialBox: A Bruteforce Attack Framework for Social Networks
- Ncrack: An High-speed Open-source Network cracking tool
- BruteSpray: A Brute-forcer From Nmap Output And Automatically Attempts Default Creds On Found Services
Continue reading
In this concise article we will learn some basics of how to use Linux Command line, so lets get started.
Requirements:
1. An open Terminal in your Linux Box. I'm using Kali Linux 2.0or you can check out this amazing website Webminal
Command: ls
Syntax: ls [flag(s)]
Function: ls is short for list. ls command is used to list the contents of a directory these contents include files, folders, and links. ls has many optional flags as well, some of them are described below
Flags: -a this flag is used to view hidden files that is those files whose names are preceded by a '.'(dot)
-l this flag is used to view file permissions, owner of the file, group of the owner, the file size, the modification date, and the filename. We'll talk more about it in later articles.
Command: mkdir
Syntax: mkdir dirname
Function: mkdir is used to create a directory (or a folder) with the name which is followed by the command
now lets create a directory in our current directory named as myfiles, how would you do that?
mkdir myfiles
which command should we use in order to verify that the directory has been created in our current folder?
ls
this will list all the files and directories in our current folder. Do you see myfiles directory listed?
Command: cd
Syntax: cd path/to/directory
Function: cd is short for change directory. It is used to navigate directories, or to make it clear it does the same thing as what double clicking on a folder do except it doesn't show you contents of the directory :(. In order to navigate or visit another directory we need to provide it's ABSOLUTE-PATH or RELATIVE-PATH you heard that, didn't ya?
Paths are of two types relative path or absolute path (also called full-path). Relative as the name suggests is relative to the current directory, so if you have to navigate to a folder within the current directory you'll just simply type cd directory_name. But what if you have to navigate to a directory which is the parent of current directory? Well it's easy just type cd .. (yes double dots, you noticed that .. and . thing when you typed ls -a, didn't you?). The double dots mean the directory above current directory (i,e the parent directory) and a single dot means the current directory (i,e the directory that I'm currently in). Now if you have to navigate two directories above current directory using relative path navigation you'll type
cd ../..
here .. means previous directory and another .. after slash (/) means the previous directory of the previous directory sounds confusing..!
The Absolute Path means full path to the file or folder which starts from root directory. Say I want to navigate to my home folder using absolute path, then I'll type:
cd /home/user
where user is the username
Now think of navigating to the myfiles folder from your home directory using the absolute path, it will be something like this:
cd /home/user/myfiles
Exercise: Create a directory project1 inside your home directory and inside the project1 directory create a file and a directory named index.html and css respectively. Then navigate to the css directory and create a style.css file inside it. At last navigate out of the css directory to home both using the relative and absolute path mechanisms.
[Trick: To get quickly out of any directory to your home directory type cd ~ [press Enter] or simply cd [press Enter]]
Command: touch
Syntax: touch filename
Function: touch is a nifty little function used to create an empty file (actually it's used to change access time of a file but everyone has got bad habits :P ). You can create any type of empty file with the touch command. If you are a bit curious about touch read the manual page of the touch command using the man touch command.
Now lets create a few files inside of our myfiles directory
touch file1 file2 file3
The above command creates three empty files in our current directory named file1, file2, and file3.
How will you verify that it has indeed created these three files in your current directory? I won't answer this time.
Command: echo
Syntax: echo Hacker manufacturing under process
Function: echo is used to display a line of text. By default echo displays a line of text on the terminal which is the standard output device (stdout for short). However we can redirect the output of an echo command to a file using > (the greater than symbol).
Now if we have to echo a line of text to a file, say file1 in our myfiles directory, we will type:
echo This is file1 > file1
The above command will echo the text "This is file1" to file1.
Command: cat
Syntax: cat filename [anotherfilename...]
Function: cat stands for concatenate (not that puny little creature in your house). The main function of cat is to concatenate files and display them on your terminal (or in geeky terms stdout). But its also used to display the contents of a file on your terminal.
Let's display the contents of file1 in the myfiles directory that we echoed to it using the echo command, for that we'll type:
cat file1
Awesome I can see on black screen contents of my file (what if your terminals background is white?), looks like I'm becoming a hacker. In case you don't see it then I suggest you should give up the thought of becoming a hacker. Just kidding you might have missed a step or two from the above steps that we performed.
Now lets say that we want to add another line of text to our file using the echo command should we use the same greater than (>) symbol? No, if we want to add another line (which in geeky terms is to append a line) to our file using the echo command we have to use >> (two greater than symbols) like this:
echo Another line of text >> file1
now to check the contents of file1 we'll type:
cat file1
OK we wrote two lines inside of the file1.
Does it mean we have to add three greater than symbols to write third line? Oh! I didn't thought you'd be such a genius.
A single greater than symbol (>) means redirect the output of the preceding command to a file specified after the > symbol. If the file exists then overwrite everything that's in it with the new contents and if the file does not exist then create one and write to it the output of the preceding command. So if you had typed
echo Another line of text > file1
it would have overwritten the contents of the file1 with "Another line of text" and the line "This is file1" would no longer be present in the file.
Two greater than symbols (>>) mean that append (remember the geeky term?) the output of the previous command to the end of file specified after >>. Now if you want to add another line of text to file1, you won't use >>> rather you'll use >> like this:
echo Third line in file1 >> file1
This is it for today. But don't worry we'll learn more things soon.
Related news
About ISPY:
ISPY is a Eternalblue (MS17-010) and BlueKeep (CVE-2019-0708) scanner and exploiter with Metasploit Framework.
ISPY was tested on: Kali Linux and Parrot Security OS 4.7.
ISPY's Installation:
For Arch Linux users, you must install Metasploit Framework and
curl first:pacman -S metasploit curlFor other Linux distros not Kali Linux or Parrot Security OS. Open your Terminal and enter these commands to install Metasploit Framework:
Then, enter these commands to install ISPY:
How to use ISPY?
ISPY's screenshots:
About the author:
- On Github: @Cyb0r9
- On Youtube: Cyborg
- On Ask Fm: Cyborg
- Email: TunisianEagles@protonmail.com
Disclaimer: Usage of ispy for attacking targets without prior mutual consent is illegal.
ispy is for security testing purposes only
Related posts
- Termux Hacking Tools 2019
- Hack Tools
- New Hacker Tools
- Hacking Tools For Games
- Physical Pentest Tools
- Hacking Tools 2019
- Pentest Tools Tcp Port Scanner
- Pentest Tools Port Scanner
- Beginner Hacker Tools
- Hak5 Tools
- Pentest Tools List
- Pentest Reporting Tools
- Hacker Tools Apk
- Pentest Tools Download
- Hack Tool Apk No Root
- Hacker Tools Free
- Hacks And Tools
- Hacker Security Tools
- Pentest Tools For Windows
- Hack Tools For Pc